- 2025 Cyber Security Predictions: Navigating the Ever-Evolving Threat Landscape
- Not Just Another List of Top 10 Metrics You Should Measure
- My new favorite headphones for swimming come bundled in a unique charging accessory
- Why I recommend this Windows laptop to creatives and professionals - even if it's meant for gamers
- This HP laptop may be the closest thing to a MacBook Pro for Windows users - and I don't mind it
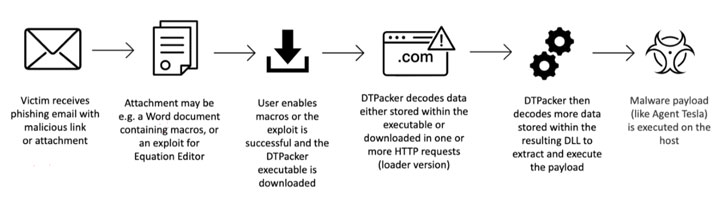
Hackers Using New Malware Packer DTPacker to Avoid Analysis, Detection

A previously undocumented malware packer named DTPacker has been observed distributing multiple remote access trojans (RATs) and information stealers such as Agent Tesla, Ave Maria, AsyncRAT, and FormBook to plunder information and facilitate follow-on attacks.
“The malware uses multiple obfuscation techniques to evade antivirus, sandboxing, and analysis,” enterprise security company Proofpoint said in an analysis published Monday. “It is likely distributed on underground forums.”
The .NET-based commodity malware has been associated with dozens of campaigns and multiple threat groups, both advanced persistent threat (APT) and cybercrime actors, since 2020, with the intrusions aimed at hundreds of customers across many sectors.
Attack chains involving the packer rely on phishing emails as an initial infection vector. The messages contain a malicious document or a compressed executable attachment, which, when opened, deploys the packer to launch the malware.
Packers differ from downloaders in that unlike the latter, they carry an obfuscated payload to hide their true behavior from security solutions in a manner that acts as an “armor to protect the binary” and make reverse engineering more difficult.
What makes DTPacker different is that it functions as both. Its name is derived from the fact that it used two Donald Trump-themed fixed keys — “trump2020” and “Trump2026” — to decode the embedded or downloaded resource that ultimately extracts and executes the final payload.
It’s currently not known why the authors chose this specific reference to the former U.S. president as the malware is neither used to target politicians or political organizations nor are the keys seen by the targeted victims.
Proofpoint said it observed the operators making subtle changes by switching to using soccer fan club websites as decoys to host the malware from March 2021, with the packer employed by groups like TA2536 and TA2715 in their own campaigns a year before that.
“DTPacker’s use as both a packer and downloader and its variation in delivery and obfuscation whilst keeping two such unique keys as part of its decoding is very unusual,” said the researchers, who expect the malware to be used by multiple threat actors for the foreseeable future.